About Us
About US
Who We Are
INFOMIX is a leading provider of industrial cybersecurity, control systems, and OT network solutions. Based in Western Australia, our team consists of highly qualified engineers, cybersecurity specialists, and project managers who are committed to delivering exceptional service and long-term value to our clients.
Our Mission
To safeguard critical industrial infrastructures by providing robust and secure engineering solutions that enable operational continuity, reliability, and performance.
Our Vision
To be the leading provider of industrial cybersecurity, control systems, and Change this to “Network” infrastructure services in the OT sector, empowering businesses to thrive in a secure digital environment.
Our Values:
– Integrity
– Excellence
– Innovation
– Collaboration

Why Choose
INFOMIX Technologies?

Industrial Cybersecurity
We offer tailored cybersecurity services designed to protect your OT and IT systems from cyber threats.
Services include:
– Cybersecurity Risk Assessments
– Threat Detection & Monitoring
– Incident Response & Remediation
– Compliance & Regulatory Consulting

Control Systems Design & Integration
We provide automation and control solutions including SCADA, DCS, PLC, and HMI systems.
Services include:
– System Design & Integration
– PLC & SCADA Systems
– Optimisation & Troubleshooting
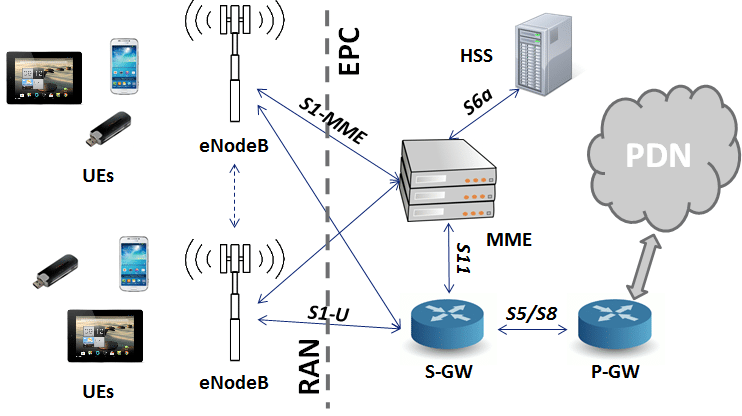
LTE Wireless Infrastructure
We provide reliable high-speed LTE communications for industrial applications.
Services include:
– LTE Network Design & Implementation
– Network Optimisation & Support
– Wireless Communication Solutions

CCTV Systems
We offer surveillance and monitoring systems for safety and compliance.
Services include:
– CCTV System Design & Installation
– Surveillance Monitoring
– Video Analytics & Reporting
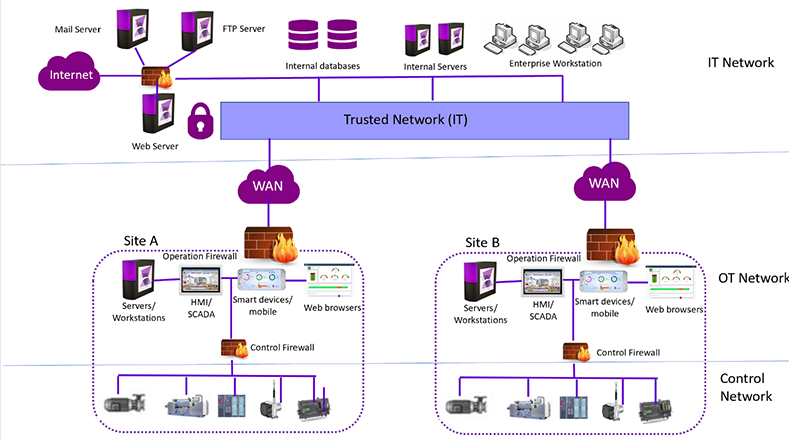
OT Network Design & Implementation
We ensure your OT network infrastructure is secure and future-ready.
Approach includes:
– Network Architecture Design
– Systems Integration
– Cybersecure Remote Access

Risk Assessment & Mitigation
We develop strategies to mitigate vulnerabilities in your OT systems.
– Threat Identification
– Risk Analysis
– Implementation of Risk Controls

